Marvelous Tips About How To Detect Keystroke Software
An android keylogger will need to be download to your device in order to work.
How to detect keystroke software. Open malwarebytes > click on the update tab across the top> get the latest updates. A software keylogger can be run in the. There are a variety of free options on the market like:
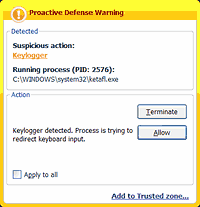
A keylogger can be either a piece of software or a hardware device that can capture the keystrokes typed on the computer’s keyboard. You may not even realize you’ve got a keylogger running on your pc until after an incident occurs. 4 keystroke detection methods click on start click on control panel select programs and features check for any suspicious file in the list of applications if the file is unfamiliar and.
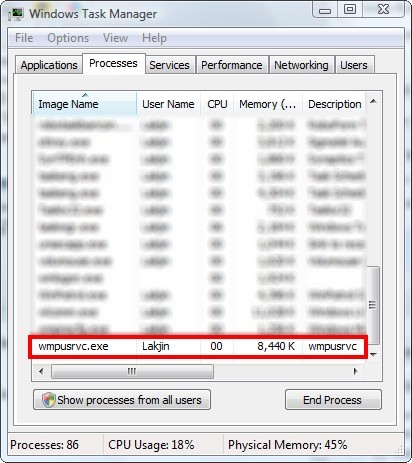
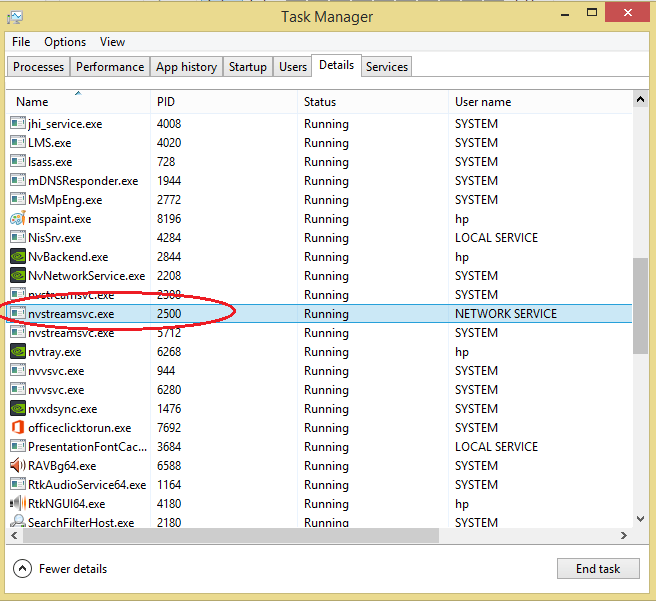
How to detect if a keylogger is installed? Usually, you can find this by searching. Use the task manager to detect keyloggers keyloggers take up processing power and have to run a process while in operation.
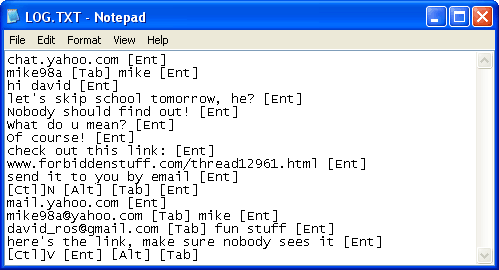
Keyloggers are unique programs that monitor keyboard activity and log everything that’s typed. The first method to detect a keylogger on your device is the use of the safe mode. Keyloggers of poorer quality (such as the malware variety) might.
On the scanner tab, make sure. So, you’ll be able to see the file in your phone’s downloads folder. You can use task manager to see processes that are running and.
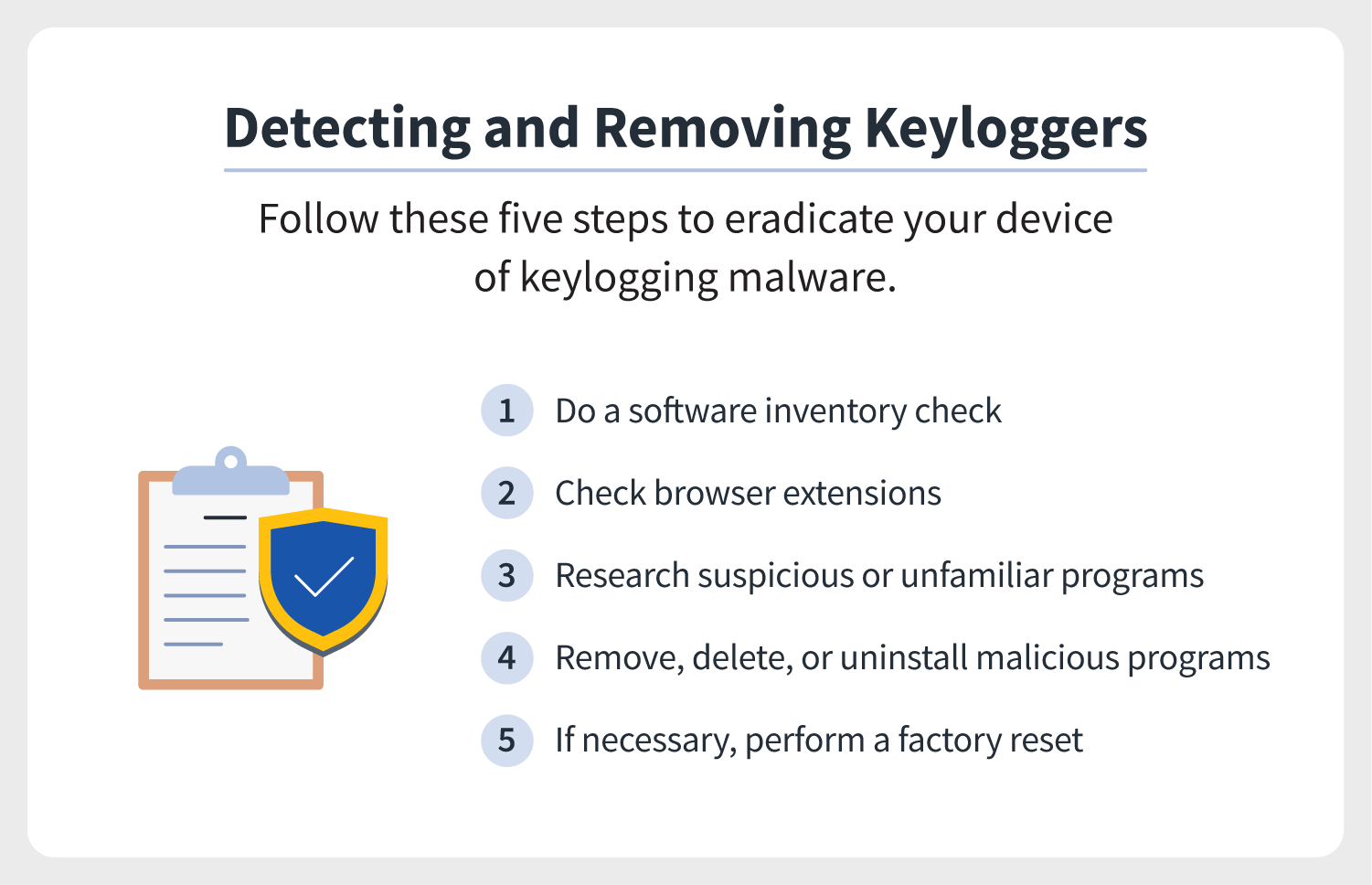
While many of these may. You can check for a keylogger in safe mode because windows only loads the basic programs. Up to 20% cash back successful keystroke logger detection starts with taking stock of the programs and processes running on your computer.
It can be tough to know which ones are legitimate and which could be. If you want to know how to track keystrokes, look no further than a keylogger. Using a public or borrowed computer.
Steps to detect keylogger & remove it from computer 1. The simplest way to detect a keylogger is to check your task manager. Methods to detect keystroke logger on pc press ctrl+alt+del when task manager opens, go to the process tab look for any malicious file in the list with a suspicious description click on it.
Well, public or borrowed computers are the best things you can avoid.